Why Password Policies Aren’t Enough

We’ve all been there. We’ve had to set a password in a system and we’ve been told it’s not strong enough. Or we finally set a strong password only to be told 30 days later that we need to change our password. Password policies are not enough to encourage good security behaviour.
A password policy enforces a set of rules for what a password should contain or how long it can be valid.
A typical password policy might look like this:
- At least 1 lowercase character
- At least 1 uppercase character
- At least 1 numeric character
- At least 1 special character
- Minimum length of 8 characters
- Password expires after 30 days
- Your last 12 passwords must be unique
For years the National Institute of Standards and Technology (NIST) have long advocated against password expiry and discouraged the use of over-complicated password rules.
Why don’t password policies work?
Security is often a trade-off. The greater the protection, the more inconvenience caused to the user. The lesser the protection, the less inconvenience to a user.
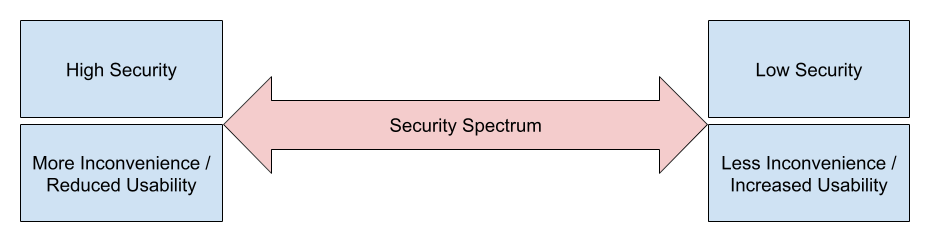
Let’s take a look at a few simple examples of security in the physical world:
- If you lock your car with the key fob, you get a level of security, and the convenience is fairly good.
- If you lock your car with the key fob and use a steering wheel lock, the security afforded is greater than in (1), but locking and unlocking your car is more inconvenient.
- If you lock your car with the key fob, use a steering wheel lock, and a wheel clamp, the security afforded is greater than in (1) and (2). Similarly, the inconvenience of locking and unlocking your car is even greater than in (1) and (2).
I
In an ideal world, security should be just enough to discourage an attack, but minimal enough not to cause unnecessary inconvenience to legitimate users.
The key problem with password policies is that they educate you on what you should do. How you achieve this is often left up to you to figure out. A typical password policy is designed to ensure a high level of complexity for passwords. This is an inconvenience for end users who have to try and remember long and complex strings of characters that they will probably have to change in a number of days anyway when the policy enforces that the password expires.
How many times have you been required to put a special character into a password and you just reach for the exclamation mark (!) because it’s the easiest to remember. How many times have you had a password expire, only to change it to the same password with a different number at the end?
Is there a better solution?
The best way to keep your team and systems secure is to provide them with:
- Education, awareness and training on security topics
- Tools to assist in staying secure
Using a tool such as 1Password means that your team can generate a complex, secure and unique password for every account that they have. With apps for Android and iOS, and plugins for all the popular web browsers, inputting a password from 1Password can be much more convenient than having to remember the credentials you used for a given system.
Conclusion
Password policies can still be a good security measure, but they should be considerate of the fact that an aggressive password policy may cause users to adopt bad practices (such as writing down a password or simply incrementing a number) to circumvent the inconveniences of the policy.
This article originally appeared on The Curve's blog. The Curve Consulting are on-demand technical experts and a trusted partner of Sify. To learn more about The Curve, please visit their website.


